This lesson is part of the Network Analysis with Batfish Course.
In this lesson, we will cover:
- How to validate ACL behaviour for a single flow.
- How to validate ACL behaviour for a large set of flow.
- How to show entries of an ACL for auditing purposes.
- How to discover ACL entries that will never be hit due to ordering.
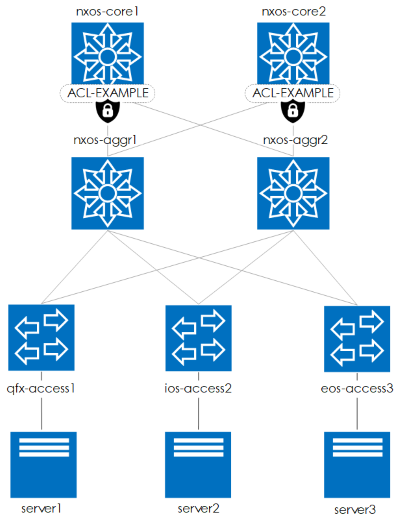
Example Topology
For this section, the snapshot we will be using is based on a topology in which ACLs are applied to the core nodes to ONLY allow traffic outbound from the environment for HTTPS, DNS and NTP (diagram below).
Below shows (for reference) the ACL configuration that is applied.
nxos-core1
object-group ip address OBJ-GRP-DNS
8.8.8.8/32
8.8.4.4/32
object-group ip address OBJ-GRP-NTP
216.239.35.0/32
216.239.35.4/32
object-group ip address OBJ-GRP-SERVERS
10.2.0.0/16
ip access-list ACL-EXAMPLE
permit udp addrgroup OBJ-GRP-SERVERS addrgroup OBJ-GRP-DNS eq 53
permit udp addrgroup OBJ-GRP-SERVERS addrgroup OBJ-GRP-NTP eq 123
permit tcp addrgroup OBJ-GRP-SERVERS any eq 443
deny tcp addrgroup OBJ-GRP-SERVERS any eq 80
deny ip any any
nxos-core2
object-group ip address OBJ-GRP-DNS
8.8.8.8/32
8.8.4.4/32
object-group ip address OBJ-GRP-NTP
216.239.35.0/32
216.239.35.4/32
object-group ip address OBJ-GRP-SERVERS
10.2.10.0/24
10.2.20.0/24
10.2.30.0/24
ip access-list ACL-EXAMPLE
permit udp addrgroup OBJ-GRP-SERVERS addrgroup OBJ-GRP-DNS eq 53
permit udp addrgroup OBJ-GRP-SERVERS addrgroup OBJ-GRP-NTP eq 123
permit tcp addrgroup OBJ-GRP-SERVERS any eq 443
deny ip any any
Access-List Questions
Batfish provides 4 questions that can be used to perform ACL based analysis. They are:
testFilters()- Returns the result of a filter processing a single flow.searchFilters()- This allows you to search across a large set of flows to determine filter behaviour.findMatchingFilterLines()- Returns entries within a filter that match any packet within a set of flows.filterLineReachability()- Return filter entries that will never be hit due to encompassing entries further up in the filter.
Import Snapshot
To import the snapshot for this section using the supplied helper script, run the following:
$ ./scripts/bf_snapshot_importer.py -p snapshots/005-acl_analysis
